GitLab
Step 1: Get your Safety API Key
Step 2: Set up a Gitlab Pipeline on your repository (If you don't have one already)
Step 3: Configure your .gitlab-ci.yml YAML file to run Safety
# PyUp Security Scans Template
# This template allows you to run security scans on your Python dependencies.
# The workflow allows running tests on the default branch.
image: python:latest
# Change pip's cache directory to be inside the project directory since we can
# only cache local items.
variables:
PIP_CACHE_DIR: "$CI_PROJECT_DIR/.cache/pip"
cache:
paths:
- .cache/pip
- venv/
before_script:
- python --version # For debugging
- pip install virtualenv
- virtualenv venv
- source venv/bin/activate
- pip install safety
run:
script:
# Install your requirements. Alternatively install via Poetry or Pipenv
- pip install -r requirements.txt
# Run Safety's environment scan
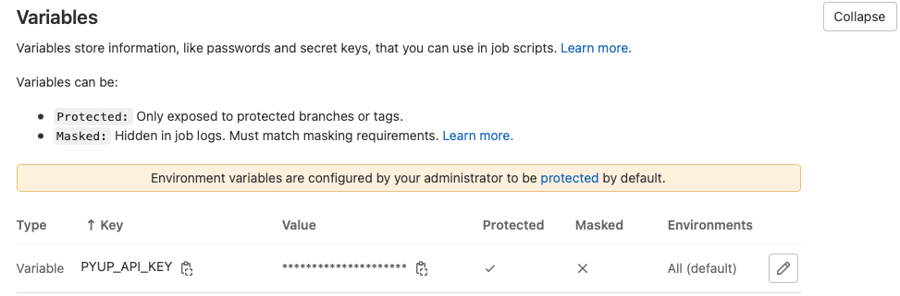
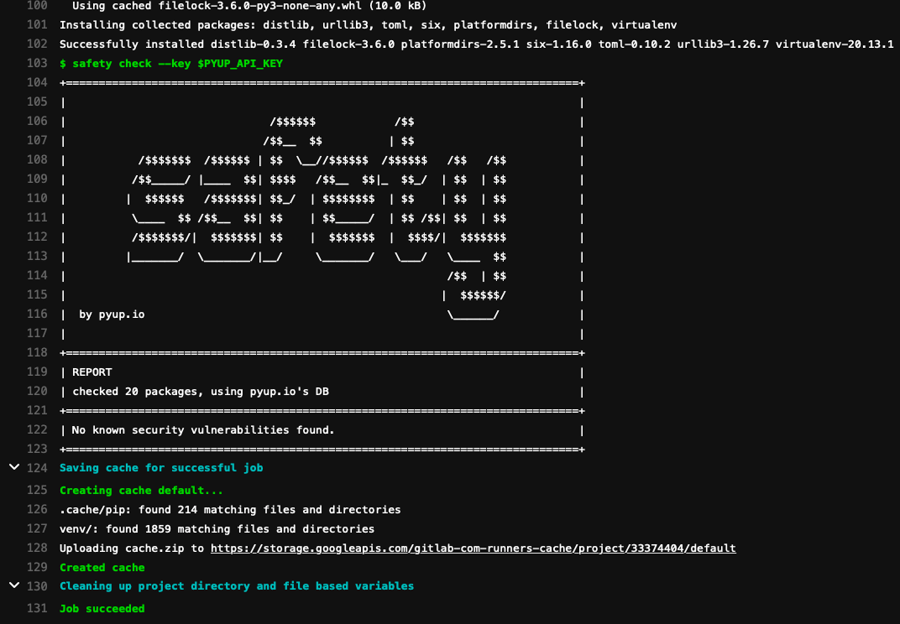
- safety --key $SAFETY_API_KEY --stage cicd scanFinal Step: Add your Safety API Key as a Gitlab repository variable
You're done!
Next Steps: Configure your Pipeline file, and learn more about Safety
Last updated
Was this helpful?